
Cisco Zero Trust Security
Balance security and usability while protecting users, networks, and applications
Frustrate attackers, not users
How Cisco enables zero trust security
Make zero trust progress while optimizing the digital experience. Zero trust helps enable secure access for users and devices and within apps, across networks, and clouds. Embed zero trust across the fabric of your multi-environment IT without compromising user experience.

Secure access without compromise
For business and security leaders struggling to reduce risk at scale, we can help create and enforce zero trust policies across all control points without compromising user experience or team productivity.
Protect multi-environment IT
Embed zero trust access controls into the fabric of multi-environment IT across users, devices, apps, networks, and clouds.
Eliminate the security-productivity trade-off
Gain higher levels of security without compromising user privacy or productivity, in the home office, on campus, and on the road.
How Cisco Enables Zero Trust
Learn how Cisco can be a trusted partner in your zero trust transformation to help your organization stay resilient against today's threat landscape and unpredictable global events, while accelerating business transformation and enabling hybrid work.
Transform your business with intuitive, secure access
4 steps to get zero trust right
Cisco believes there are four essential zero trust functions: establish trust, enforce trust-based access, continually verify trust, and respond to change in trust.
Build trust for zero trust across the stack
Choose a partner with the breadth of zero trust capabilities to cover today's and tomorrow's use cases across the security stack.
Break down silos with a connected platform
Securely connect users, devices, and IoT to apps and data across multiple clouds and networks for a cohesive approach.
Cisco walk the walk, and it pays off
Cisco own zero trust journey has unlocked US$3.4M in annual productivity savings and prevented 86,000 monthly system compromises by securing user and device access for our workforce.
Zero trust security across the edge and beyond
Secure user access, unify policies, segment networks and workloads, and accelerate threat detection and response, across the enterprise.
User and device security
Protect user and device application access across IT and IOT:
- Secure Access by Duo
- Secure Endpoint
- Secure Email
- Cyber Vision
- Vulnerability Management
Network and cloud security
Implement network segmentation and protect access to the cloud:
- Identity Services Engine (ISE)
- Umbrella
- Secure Firewall
- Secure Network Analytics
Application and data security
Enforce microsegmentation policies in apps and deepen visibility:
- Secure Workload
- Secure Cloud Analytics
Build Business Resilience With Zero Trust
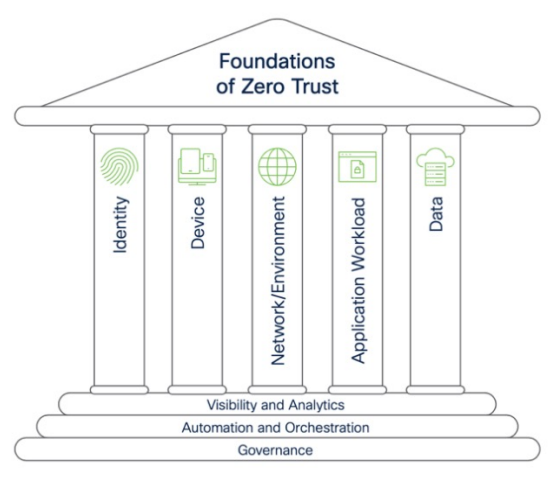
With Cisco, organizations can embed zero trust across the fabric of their multi-environment IT ecosystem to secure trusted access for users, devices, apps, networks, and clouds.
- Frustrate attackers, not users. Combine the highest levels of security with an easy user experience, eliminating the trade-off between security and productivity that typically impedes zero trust adoption.
- Connect policy across control points. Leverage a connected platform with unified policy lifecycle management across users, networks, devices, applications, and clouds.
- Share signals across environments. Unify security visibility across mixed IT ecosystems and on-premises infrastructure.
- Quickly adapt to change in risk. Continuously monitor your entire IT environment to detect abnormal behavior across users, application workloads, and your network.
- Accelerate threat response. Detect, investigate, and remediate threats through real-world contextual risk, and automated and orchestrated workflows across SecOps, ITOps, and NetOps teams.
- Simplify security. Gain visibility and control with integrated and open solutions that support Cisco and non-Cisco products to maximize existing investments.
Zero Trust Security Across Multi-Environment IT
Too many point solutions offer limited zero trust capabilities, ultimately increasing friction and complexity for users and IT admins. And cloud-only approaches fail to account for critical applications housed on-premises or in private networks. The truth is that zero trust cannot be achieved with a single product or use case.
For organizations struggling to reduce risk at scale, Cisco simplifies the zero trust journey. Cisco meets you where you are to achieve desired zero trust outcomes - whether securing hybrid work, protecting cloud environments, gaining visibility into devices, improving the access experience, or meeting regulatory compliance.
Our customers make zero trust progress while creating a seamless user experience. By connecting shared signals across all control points of user, device, network, cloud, application, and data, organizations can implement consistent security policies across the multi-environment IT reality. With capabilities such as identity-based access, unified network access control, micro-segmentation, behavioral monitoring, and more, Cisco provides a path to zero trust maturity.
Adopting zero trust security is transformational. Changes in mindset come first, then toolset.
This guide is designed to help you find quick wins in your zero trust journey and continue making progress toward zero trust security. By studying enterprises with mature implementations of zero trust, we found:
- Zero trust progress is possible regardless of organization size or IT infrastructure complexity.
- Organizations with high zero trust maturity are twice as likely to achieve business resilience.
- Plus, these organizations are twice as likely to excel at the five key security practices:
- Accurate threat detection
- Proactive tech refresh
- Prompt disaster recovery
- Timely incident response
- Well-integrated tech
Cisco Zero Trust Workshops
Establish trust at the point of access
In a zero-trust security approach, every access attempt is treated as if it's originating from an untrusted source. Cisco is here to help you build trust. Join our security experts for hands-on workshops to learn how you can successfully adopt a zero-trust strategy.

About our zero-trust workshops
What are they?
Virtual workshops that can help you understand the adoption journey, engage in hands-on activities, and develop an action plan.
Who should attend?
Anyone who is responsible for security strategy, procuring security solutions, or driving the adoption of a security model.
What to expect?
An interactive experience with practical activities and discussions that help you learn how to adopt zero-trust security.
Choose your workshop
Workshops are tailored to varied levels of understanding and approaches to adopting zero-trust security. Pick the workshop that works best for you.

Strategy and Planning
Learn how to accelerate your zero-trust journey, perform a gap analysis, and network with peers to share strategies and techniques.

Implement and Execute
Learn how to implement a zero-trust strategy that delivers results, explore use cases in a hands-on lab, and discover best practices.

Zero Trust: Going Beyond the Perimeter
In this guide, you'll learn:
- The fundamentals of a zero-trust approach to enterprise security
- The three pillars of zero trust - workforce, workloads and workplace - and their differences
- Risks addressed by each pillar of zero trust
- Options for implementing each of the three zero-trust pillars
- Proposed maturity models to achieve zero trust for the workforce, workloads and the workplace
Zero Trust Evaluation Guide: For the Workforce
In this guide, you will learn how to evaluate a solution based on:
- User Trust
- Device Visibility
- Device Trust
- Adaptive Policies
- Access to All Apps


